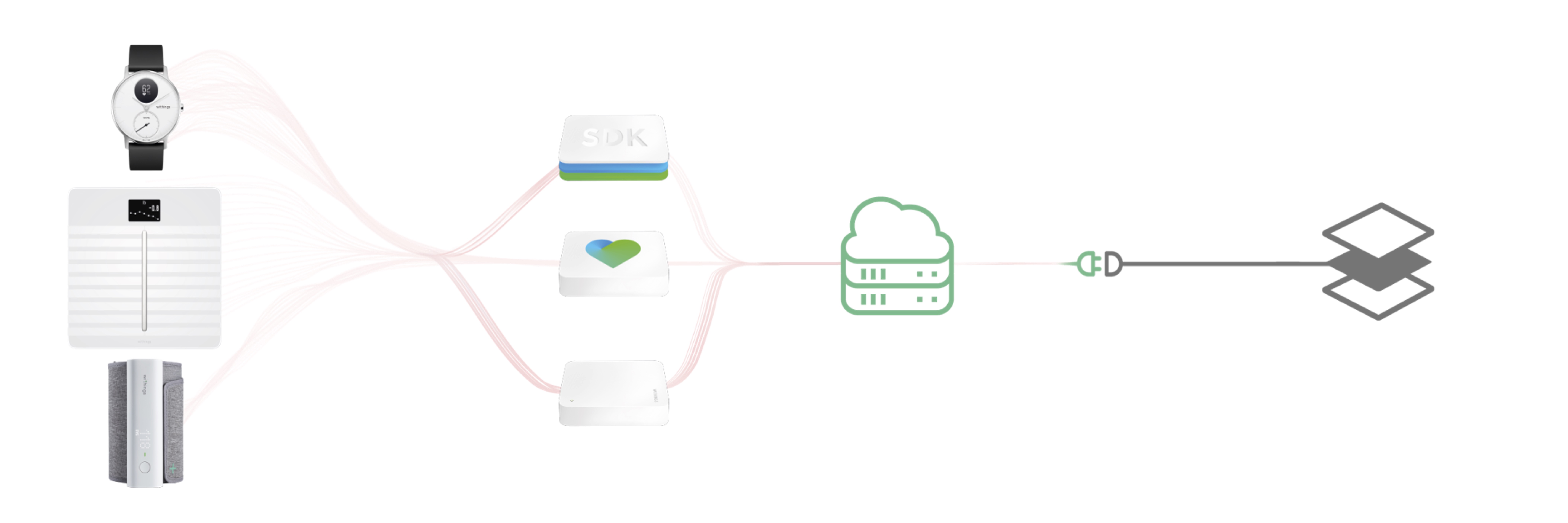
👋 Welcome
Welcome to Withings Developer Portal. Discover the services we offer, and all the tools you need to integrate them. You will be able to create applications using Withings devices and the wide variety of health data they record, including weight, body fat, activity, sleep, blood pressure, heart rate, ECG, PWV, and more.
07/07/22 - New Postman collections :
Pro integration solutions now also get their own Postman collections! You will find the Postman collection for your use case inside the corresponding integration guide. Feel free to fork the collections and create pull requests to enhance them!
04/15/22 - New Developer Dashboard :
With Withings new Developer Dashboard, it's never been easier to integrate Withings solutions. Learn more